Your company’s computers and networks contain a collection of personal, sensitive information, which if compromised, could mean disaster for your business.
Cyber attackers are constantly on the prowl for vulnerabilities, oftentimes targeting smaller businesses, who they deem as easier targets. That means, no matter your industry, your company needs a powerful cybersecurity strategy.
Here’s five questions to access your current level of protection:
1. Are you protected against ransomware attempts?

Ransomware is a cyber threat where an attacker encrypts your data and prevents you from accessing certain files, or even your entire system. Usually, the attackers will demand a ransom, or a sum of money, to unlock your data.
You may have heard of it, but how are you protecting your company from this threat? Does your cybersecurity policy involve routine port scannings, ensuring you have proper internet filters and remote network control?
Here’s seven ways you can quickly and effectively reduce your ransomware risk.
2. Does your team know what a phishing attack might look like?

The term “phishing” is an analogy to the idea of fishing for information, getting its name from sly thieves who attempt to steal sensitive information by impersonating a someone you trust. Cyber criminals can poise as important figures, like your boss, and demand you immediately open an attachment or send over private company information.
Do your employees know how to assess an email address and know if it’s suspicious? Attackers may try to imitate brands in their email headers, or in the sender’s display name. If your boss’s email is john@access.com, you may receive an email from john@assess.com and not notice the difference if the bolded name next to it displays your boss’s first and last name.
Read more tips for spotting clever phishing scams and educate your team.
3. Are you blocking malware threats, in all forms?
Ever heard of malvertising? This is a term coined for online advertisements that are injected with malicious code. If one of your employees curiously clicks on an ad, this code will immediately search their computer for vulnerabilities. (Don’t think people don’t click on ads, either. They can track your search history and serve up something you’ve already searched for, intimidating trusted shopping sites, like say, Amazon.)
Using a powerful antivirus or ad blocker is a great precautionary strategy, but your company should also frequently update its operating system, browsers and plugins too. Oftentimes these updates are made to patch security vulnerabilities and should not be ignored.
Here’s ten ways to prevent a malware infection.
4. Are your employees able to access http:// sites that are not secure?
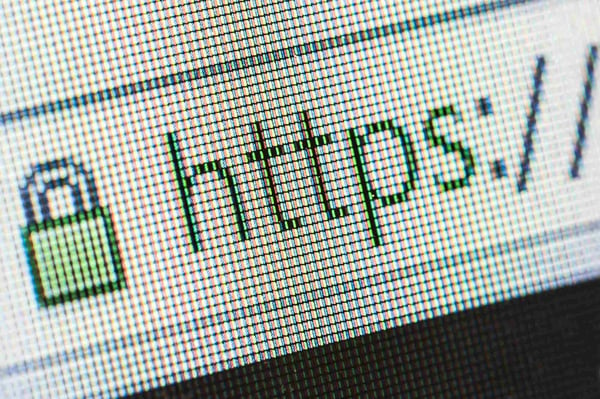
The “s” after http:// in a website’s URL stands for secure. Websites with this important “s” will encrypt the data you submit on their site. This means that cyber attacks can’t see the private data you entered, such as passwords, email addresses or credit card numbers.
Your employees could be making a business transaction online, or signing up to a site with a company email, and unintentionally give criminals access to your systems. We strongly suggest you block unsecure websites, across all browsers. Remember, Firefox might be your standard, but if an employee decides to use Chrome and you’re not safeguarded, you could be exposed.
Here’s a great extension for Chrome users, which automatically switches http:// sites to a secure domain— but this is only one of many preventative measures you organization should be taking. Also read these tips from Google about securing your own site with HTTPS.
5. Are you protecting your data with multiple layers of security?
A cyber attacker might be able to cross a metaphorical river to get to your data, but what if your treasure was also behind a wall, past a dangerous dragon and locked in a chest? In this way, your systems should be like a fortress, with multiple layers of security measures to stop trespassers.
Your first layer of defense might be made up of firewalls, ad blockers and traffic filters, while your second layer two-factor authentication protection, antivirus and anti-malware. Lastly, encryption— and let’s not forget an external or cloud-backup for safe measure.
With the right cybersecurity strategy, your empire will never fall.
It Takes an Army
Is your business protected against cyber attacks? These five questions only address a few concerns.
Are you also actively implementing:
- Application system patching
- Content filters
- Password management and policies
Think of our team at Access System as the army you need to safeguard your data. Our cybersecurity experts are here to protect your assets and consistently monitor your systems.
Explore our Cybersecurity page to learn more. We can create a customized strategy to fortify your business.
.png?quality=high&width=3192&height=1279&name=Copy%20of%20Untitled%20(63).png)


