You’ve heard of malware, but what it is? Malware is short for malicious software, a term which covers a wide range of online threats and cyber attacks.
Malware can be sent via email, added to a website to infect visitors or hidden within a seemingly safe program. Once it gains access to your device, attackers use it to steal or leak sensitive data, or use your internal information to target others.
Don’t let a cyber attack mean disaster for your business. Malicious software comes in many shapes and sizes— and it’s up to you to be prepared. Here’s four common forms of malware:
Viruses
Though often incorrectly used as a sweeping term for any online attack, viruses are a specific form of malware.
There’s many types of viruses, but oftentimes they attach to files. Anytime you open the file, the virus is running, injecting malicious code into your network. But, unfortunately, they can get more complex. Some memory resident viruses bury themselves into your computer's memory, meaning, whenever you run your operating system, the virus is working— sometimes deleting your files to make room for more malicious replication!
There’s two really scary things about a virus:
-
It executes itself. The virus overrides the executive path of the original file, running upon opening, without you giving it permission.
-
It replicates itself. The virus can inject multiple files on its own. It can replace your files’ “good code” with malicious code. Unbeknownst, you send an infected file to a friend and the virus spreads!
Your business probably has antivirus software, but does it scan files in real-time, instead of manually? Viruses are most commonly contracted by opening an injected .exe file. If an attachment is automatically scanned before opened, you’ll likely know if it’s a threat before clicking it, instead of trying to remove it later.
Ransomware
We’ve all likely heard of ransomware. It’s malware that encrypts your files, so you can’t access them and demands payment before giving them back.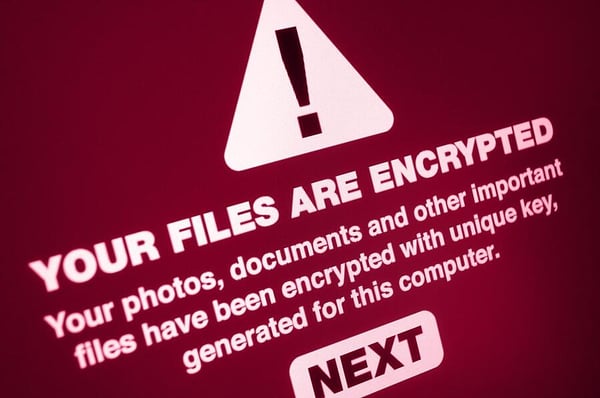
Attackers usually give you malware by sending infected attachments via email, but aggressive forms of ransomware exploit security holes without needing you to click on anything. Here’s seven ways to reduce your risk of getting ransomware.
Trojans
Remember how the Greek army hid inside of a hollow, wooden Trojan horse? They were wheeled into the city of Troy, and once in, jumped out and overtook the city in the middle of the night. In the digital world, a Trojan is a piece of software that appears safe (likely attached in a phishing email), but once downloaded or opened, reveals itself as something else.
You might be thinking, “wait, a Trojan isn’t a virus?” Correct, though often referred to as Trojan viruses, Trojans are not viruses, but rather, a type of malicious software. As we just learned, viruses can execute and replicate themselves. Trojan software cannot replicate itself. A hacker (or you, accidently!) must intentionally send that exact infected file to another person for it to spread, and it won’t attach to other files.
Some common forms of Trojans are “backdoor” Trojans, which creates a backdoor to your device. A cyber attacker can use this to gain access, sometimes right before your eyes! Imagine how scary it would be to see someone take over your screen and go through your files. Trojans can also flood your website with so much traffic it takes down your network (called a DDoS attack). Sometimes hackers will use your computer as a proxy to conceal their identity or to send out spam, too.
Spyware
This is a form of malware that runs in secret and gives attackers access to “spy” on the things you do on your computer including your web activity. Spyware can often be paired with other malware to gain even better access to your device.
Spyware code sends the information back to the cyber criminal, who uses this sensitive information to steal your passwords or credit card numbers. This form of malware stays hidden, until the attacker gets the information they need. Then, the hacker can frame you with a ransomware message, or discover your password and change your security settings to allow remote access and take over your device.
You could pick up spyware just like you could a Trojan, from opening a corrupt file, clicking something on an infected website, etc.
Do you Have the Right Cybersecurity?
There’s more forms of malware than these. For example, adware is malicious software that forces you to interact with an advertisement, or computer worms can automatically cue itself to send out to your contacts. Luckily, we know of them all!
To get started, review our cybersecurity checklist. Antivirus software, firewalls and ad blockers can help keep malware at bay, but they’re often only a good first layer of defense, best paired with other cybersecurity strategies.
Explore our Cybersecurity page to learn more about all of our protection measures.
.png?quality=high&width=3192&height=1279&name=Copy%20of%20Untitled%20(63).png)


